Detection and Analysis is a Continuous Process of a Cyber attack
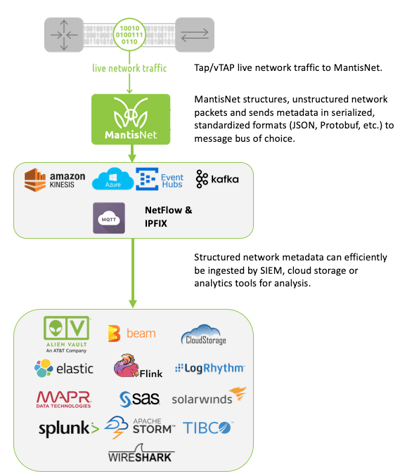
Digital transformation and the growing complexity of IT environments present new vulnerabilities that can be exploited by attackers for reconnaissance, delivering malicious payloads or to exfiltrate data. Using live network traffic for analysis to expose hidden malicious or anomalous activities and security threats among the complexity is fundamental for improved detection and response. So much so, that Gartner recently published an inaugural market guide for network traffic analysis (NTA), to help organizations understand what to look for (more on that later). Network traffic analysis uses network communications and their protocols for detection, identification and analysis of cybersecurity threats and potential operational issues. As you'll read, we propose doing this in real-time, with wire-speed network data and analytics to meet the demands of digital business and to gain an edge on reducing mean time to detect (MTTD) / mean time to respond (MTTR). Continuous visibility, detection AND the ability to react to network traffic is becoming more critical to protect corporate assets in real-time, especially as the increased volume and speed of data inundates traditional log analysis and alerting mechanisms managed by SOC/NOC teams. Since the network is a source of ground truth and the transportation mechanism for suspicious/malicious traffic, why not leverage new technologies and techniques to not only detect and manage anomalies but to take action in real-time? One approach is to leverage a zero-trust approach with real-time network traffic inspection for real-time analysis and remediation. Real-time network traffic analysis helps engineers, operators, administrators, and analysts better identify anomalies and suspicious traffic patterns that could be an indication of compromise (IOC) or an infrastructure component malfunctioning. Whatever the reason behind the anomalies or suspicious traffic, having accurate situational awareness and analytics empowers administrators with tools to make an informed, intelligent and timely decision in regard to containing and resolving potentially critical issues. Leveraging real-time network traffic data, where you have accurate visibility into the network layers 2 – 7 (infrastructure through application) for both north-south and east-west traffic, is becoming a critical capability to gain true, continuous, visibility into network traffic behavior for detection and response. Coupling real-time visibility for identification with interactive remediation for response to take action on suspicious or malicious traffic can improve network operations and cyber defense. Network engineers and security specialists have traditionally used offline logs, packet capture and packet inspection technologies to analyze network traffic; but those legacy approaches leave organizations exposed and are now giving way to a new generation of real-time continuous monitoring and remediation solutions that leverage real-time traffic monitoring and the latest generation of streaming, event-based analytic tools which are foundational to both Operations and Security teams. Getting the live network traffic for network traffic analysis is accomplished by placing physical or virtual sensor technology (via TAP/vTAP) anywhere on your network where you want to start exploring traffic to feed your analytics tools (as shown in the graphic to the right). The technology not only looks at the live traffic, but also provides a feedback path if the traffic is determined to be anomalous or malicious –for follow-on processing, further examination, processing, or termination. Gartner recently published an inaugural Market Guide for Network Traffic Analysis (NTA) for security and risk management professionals. It provides good insights into what to look for and apply to IT environments to bolster situational awareness and cyber defense. Many of the capabilities and recommendations they make are already engineered into our solutions and provide a great foundation for organizations as they evolve to implementing a zero-trust approach to real-time network intelligence and response. Some of the criteria and recommendations for NTA that we enable: The criteria and recommendations from Gartner contained in the Market Guide provide a focus on network behavior to expose sophisticated attackers, where network traffic behavior can help teams identify unknown threats and supplement signature-based detection for known threats. Additionally, consideration should be given for tools with decryption capabilities to best investigate SSL/TLS or TLS 1.3 traffic that can be identified leaving your network. For operations and security administrators; real-time, continuous network traffic monitoring and analytics can solve the most challenging mysteries. Because attackers can oftentimes hide, or operate in "plain sight" with sophisticated exploit and countermeasures; having high resolution visibility into network traffic that scales and can identify encrypted traffic for monitoring and analytics can answer questions such as "When did this attack start?" "What data did attackers collect?" and "How did they breach our cyber security defenses?" While monitoring tools alert administrators to previously occurring events, continuous real-time analysis provides information on what is happening, as it is happening. Using analytic tools empowers security administrators to better analyze, identify, react and contain anomalies and threats in-real time, to minimize, or avoid damages or losses. Network traffic analysis provide administrators with deeper insight into the traffic traveling across their network. Understanding traffic patterns is one part of data security that can provide administrators with better situational awareness. The second part is to harness network data for actionable, real-time decisions to identify, contain and resolve incidents. This requires much more awareness and control than relying on offline tools, third-party algorithms and applications to alert administrators should suspicious patterns be detected. Frankly, given the increasing sophistication of IT infrastructure and the speed at which malicious actors can operate, the risk of not moving to a continuous zero trust real-time detection and response architecture will be manifestly counter-productive, resulting in unacceptable increases in MTTD/MTTR, putting organizations at significantly greater risk. Ultimately, the goal is to stay ahead of threats; time is of the essence. Evolve your processes to utilize continuous wire-speed network traffic analysis that deliver, actionable intelligence, dynamic control and scalable connectivity. Contact MantisNet if you want to discuss how to adopt real-time network intelligence for network traffic analysis.What is network traffic analysis (NTA)?
Combine visibility with interactive response in real-time
Why Continuous, Real Time Network Traffic Analysis and Monitoring
Topics: cyber security, Real-Time Monitoring, mantis, cybersecurity
Source: https://www.mantisnet.com/blog/network-traffic-analysis
0 Response to "Detection and Analysis is a Continuous Process of a Cyber attack"
Post a Comment